Introduction
In the context of big financial scandals underlying the economic, financial and other (political, social, etc.) crises, the quality of the financial and accounting information as well as the obtaining of an accurate image of the company’s financial position and performance represent the main wish of the stakeholders. According to the practices of corporate governance (Russell, 2009), which involves the wish to reduce the information asymmetry between principals and agents, the responsibility of the company’s financial statements certification fully rests with the financial auditor, the acknowledged, independent specialist, whose objective opinion assesses the compliance of the reported financial standings with a reference accounting framework (IFAC, 2009).
From the point of view of Lending Credibility Theory (Hayes et al., 2005), the auditors and the audit companies are regarded by the public as vectors of credibility increase with regard to financial standings, and according to Theory of Inspired Confidence the audit services must support the stakeholders’ trust in the managers of the audited companies and their actions (Limperg Insitute, 1985). These audit services are part of the monitoring activities within the company and significantly contribute to the decrease of information bias (Watts and Zimmerman, 1978).
However, as a result of the big financial scandals (among these also are Cendant 1998; Microstrategy 2000; Xerox 2000; Enron 2001; Adelphia 2001; Aol 2002; Duke Energy 2002; Merrill Lynch 2002; WorldCom 2002; Parmalat 2003; AIG 2004; Lehman Brothers 2008; Satyam Computers Services 2009) the public opinion’s attention has been oriented worldwide to auditors, as well, since they were considered responsible to a smaller or greater extent (due to the complicity of the big audit companies or the incapacity of detecting frauds) for the financial losses inflicted on defrauded companies (Ball, 2009).
In this respect, this study aims to test the extent to which the affiliation of a client to one of the four big audit company members of Big 4 (consisting of Ernst&Young, KPMG, Deloitte and PricewaterhouseCoopers) has significantly contributed to the occurrence of financial frauds, due to the complicity or incapacity of the auditor to detect and report them. Applied on the level of a sample of 200 companies, defrauded and not defrauded, quoted on New York Stock Exchange (NYSE), the study combines the qualitative analysis with the quantitative one by using advanced statistical methods (multiple correspondences factorial analysis, logistic regression analysis) to validate the work hypotheses and obtain research results. The use of this study and thus of the research results consist of offering pertinent information to all stakeholders regarding the influence the audit company members of Big 4 have on prevention and detection of financial frauds within audited companies. Based on this information, stakeholders can assess the competence of an audit company, as well as the extent to which they can rely on the audit opinions expressed by the big audit companies forming Big 4.
Theoretical Perspectives on Financial Fraud
With reference to USGAAS (United States Generally Accepted Auditing Standards), expressed starting with 1972 by AICPA (American Institute of Certified Public Accountants), through the definition stated in Statements on Auditing Standards (SAS 99 – Consideration of Fraud in a Financial Statement Audit), financial fraud is considered a deed deliberately committed by one or several individuals from management, governance-assigned persons, employees, or third parties, which involves the use of deceit in order to obtain an unjust or illegal advantage (Bragg, 2010).
According to the definition of Bierstaker (2009), financial fraud is an illegal act, which consists in the deliberate deceiving, the deliberate appropriation of sums against the deliberate agreement of a second person or the deliberate forgery of a document, accompanied by their dissimulation, which can eventually result in the infringement of the rights and interests of a person or company. According to Lenard et al. (2010) and Seow (2009), the importance of this definition’s deliberate (voluntary), illicit character (resulting from the illegality of the phenomenon), as well as the dissimulation wish (by means of which the deeds can be hidden or erased) can be underlined.
The International Standards on Auditing (ISA) 240 (The Auditor’s Responsibilities Relating to Fraud in an Audit of Financial Statements) issued by IFAC (International Federation of Accountants) makes the difference between fraud and error, consisting of the intention of the committed act, in the case of assets misappropriation or fraudulent financial reporting (Bragg, 2010 and IFAC 2009). Bernardi (2009) considers that the distinction between frauds and errors comes from the involuntary character, by omitting figures or information of different character than the financial frauds, which involve the existence of a deliberate deed committed by one or several governance officials, employees or third parties, with a view to obtaining illegal advantages. Also in this case are pinpointed three main elements which cause the occurrence of fraud: the voluntary element (different from error), the purposeful dissimulation of facts (during its entire duration), and the setting of an operating mode.
Having as starting point Donald Cressey’s study (1953) regarding the extents of financial fraud and their grouping as a fraud triangle (fraud triangle), the audit standards adopt this tridimensional perspective of fraud caused by: opportunities, pressures (motivating factors) and reasoning (attitude). Gallet (2010) considers that the ones who know the company environment in detail, the information system or the control mechanisms and possess a series of technical abilities have the opportunities to commit fraud. Secondly, the pressures on the ones that commit frauds are determined by the key appointment of persons that prove not to efficiently master essential domains, some personal failures or some financial frustrations of the employees (Gallet, 2010). Thirdly, Gallet (2010) asserts that the reasoning of the one committing the fraud takes into account his individualistic behaviour and the attempt to find justification for its illegal deeds.
Although ACFE (Association of Certified Fraud Examiner) makes the distinction between three types of fraud (frauds on financial reporting, assets embezzlement and acts of corruption), the audit standards (SAS 99 and ISA 240) only admit the first two, as they have a significant influence on the financial position and performance. Most of the times, the frauds on financial reporting are caused by the managers (Cheng et al., 2009), the damage value is considerable, and their objective is to forger the financial standings, in order to deceive investors and partners regarding the reliability of the company. The frauds committed by managers aim to distort the reality synthesized in the financial standings either by underlining an exaggerated result, or by presenting an improved balance or combinations of the two methods (Singleton and Singleton, 2010). Less known, but also less important, the frauds on assets are committed by employees. Taking advantage of the positions in the company or the access to certain data they can change, the employees steal assets from the company they work for by using illegal means (Rezaee et al., 2010).
Among the actors involved and who are responsible for these phenomena, Bernardi (2009) mentions: companies (under all organizational forms; due to the control and internal audit system, environment and organizational culture), external controllers (from external auditors, chartered accountants to the state control bodies, by deviating from the ethical code and deontological standards) and banks (by mostly accepting the fraudulent means of payment).
For their detection and prevention, Bernardi (2009) asserts that the main elements, which can signal any fraud scheme, must be identified. Internally, fraud schemes aim to the development of the main economic and financial processes: acquisitions-suppliers, sales-customers, cash office-treasury, immobilizations and stocks, salaries-payments. Within the acquisitions-suppliers process, the financial frauds represent the creation of a fictitious vendor, redundant payments, unjustified acquisitions, forgery of payment means and other acquisition-related frauds. Regarding the sales-customers process, the main schemes are related to checks embezzlement, money transfer at accounts level (lapping), invoicing techniques and generating of fictitious customers (Bierstaker et al., 2006). The financial fraud schemes related to the cash-treasury cycle treat skimming, cash errors, bank accounts (at deposit level or kitting), and the process involving economic and financial operations at immobilizations and stocks level can be vulnerable in front of stocks or immobilizations embezzlements (Bierstaker et al., 2006). At salaries-payments level the main fraud schemes are the ghost salary, the double salary payment, the fictitious employees, unreal commissions and reimbursements of unjustified expenses (Bierstaker et al., 2006).
At company level, the financial standings contain more and more complex information, which is necessary for making internal (managerial) or external (decisions of third parties, state, future shareholders or civil society) decisions. Financial standings-related frauds have caused both the most publicized scandals and most of the times economic and financial crises. This kind of fraud has thus resulted in the investors losing their trust in the ability of the company to continue its activity and generate cash flows in a predictable future. In order to prevent the distortion of synthesized information in the financial standings, the internal control system of the company is considered to be a panacea for fraud eradication, associated with the publishing requests of intermediate, quarterly or half-yearly situations (Huang, 2009). A reliable piece of information consists of a series of costs associated to its obtaining, which are justified by the indispensable character for accomplishing financial analyses, with direct impact on the quotation of prices. Although the methods used by the ones committing frauds are mostly the same, their detection becomes more and more complex and difficult to analyze, due to the deontological, social and psychological implications.
Krambia-Karpadis et al. (2010) are of the opinion that better safe than sorry and say that the prevention of frauds must be put ahead their detection due to the costs associated to the fraud risk, the impossibility to retrieve the embezzled goods and the time and money consumed in legal actions against the culprits. Moreover, the identification of the risk factors which lead to fraud committing, the promotion and implementation of an ethical environment and behaviour, the development of a reliable control system and the careful selection of collaborators (internal and external) are the premises for the development of a performing financial fraud prevention system.
The Role of the Financial Auditor in Preventing and Detecting Financial Fraud
Ever since its emergence as a profession and until the forties of the 20th century, the main responsibility of the auditor was to detect frauds (Dowler et al., 1912 and Walton et al., 1916). Based on that responsibility, The Policeman Theoryconsequently emerged, according to which the auditor is regarded as a policeman, whose role is to check the accuracy of financial standings, for preventing and detecting frauds (Hayes et al., 2005).
Currently, according to ISA (IFAC 2009) and USGAAS (Bragg, 2010), the main target of the audit mission is to increase the trust degree of the final users of the financial standings. Within the audit report, the financial auditors must express a professional, objective and independent opinion regarding the compliance of the audited financial standings with a required accounting reference (Ebrahim, 2010). But as far as professional fraud and fraud risk are concerned, the concerns to detect and control these deeds are pretty active and clean-cut by means of standards that are dedicated to this aspect, no matter whether we are talking about USGAAS or ISA (Carpenter, 2007).
The first step in the fraud risk evaluation within the financial audit mission was represented by the issue of the standard SAS 82 in 1997 (Consideration of Fraud in a Financial Statement Audit), whereby the distinction between fraud and error was made. At the same time, an initial list of potential fraud risks that may occur on company level was offered. IFAC consequently issued ISA 240, directly inspired by SAS 82. In its new version of 2009, ISA 240 brings a series of amendments to the old IFAC standard by offering examples of fraud risks, analytical procedures for fraud detection, circumstances which can signal their presence, as well as anti-fraud programs and controls. In parallel, SAS 99 replaces SAS 82 and introduces the brainstorming concept, accomplished on audit team level in order to assess and determine whether a customer company may be affected by frauds and determine the adjacent fraud risks (Carpenter, 2007).
By virtue of the audit standards ISA 240 or SAS 99) the auditor’s main objective is not to prevent and detect financial frauds, but to express an objective, professional and independent opinion regarding the accuracy of the audited financial standings. ISA 240 also mentions that, throughout his mission, the auditor must make sure that the fraud risk shall not significantly influence the final opinion of the audit report (IFAC, 2009). In the USA, financial auditors are supported by adopting Srabanes-Oxley Act 2002 (SOX) in preventing and detecting frauds. This legislation requires the organizing of an audit committee within the audited company, the adoption of an ethical code, the assurance and implementation of an internal functional control system, the organization and institutionalization of the internal audit.
In order to evaluate the fraud risk and its implications on the auditor’s final opinion, a series of audit evidence is necessary, defined through ISA 500 (Audit Evidence). The audit evidence represents all the information used by the auditor to substantiate the audit opinion (IFAC, 2009). Moreover, the audit evidence must fulfill a series of quantitative and qualitative requirements: sufficiency and appropriateness. Sufficiency measures quantity in evaluating fraud and audit risk, and appropriateness makes sure that the audit evidence corresponds to the needs and target of the audit and also takes into account the necessary quality in the way they are obtained (Hayes et al., 2005). In this respect, an increase in the quantity and also the quality of evidence elements is necessary for reducing the fraud risk.
According to Soltani (2003), the main means used to obtain the audit evidence are: inspection, observation, external confirmation, recalculations, re-performance of some operations, controlling, analytical procedures and interviews. These can be applied by means of special programs, questionnaires and trial balances (Soltani, 2003).
During the mission, by means of the analytical procedures, the auditor gets to know the entity and its environment as well as the internal control system and detect the significant deviations at the accounting assertion level (Pickett, 2006). The financial-accounting deviations can be signaled through the analysis of the main financial and trend rates, including the results of the fluctuations and relations investigations which do not comply with other similar relevant information or which feature significant deviations from the projected data (Hayes et al., 2005).
The analytical procedures are defined in ISA 520 (Analytical Procedures) as evaluations of financial information through the analysis of the plausible relations between the financial and non-financial data (IFAC, 2009). Hayes et al. (2005) consider that the analytical procedures comprise the investigations regarding the fluctuations or relations which are discordant compared with other relevant information or differ by a significant sum from the expected values. SAS 56 suggests the use of advanced statistical methods in order to obtain pertinent models by means of which comparisons on branch or reporting periods level can be accomplished (Bragg, 2010). The financial auditor can thus identify the unusual events or transactions, balance-related or business-related changes, random fluctuations or probable accounting distortions (Bragg, 2010).
According to the above-mentioned, it can be assert that the auditor must play an active role in preventing and detecting financial frauds, as he is a guarantor of the accuracy of the reported financial-accounting standings. Moreover, by virtue of the audit standards and the ethical code of the profession, the auditor must serve all stakeholders’ interest by applying the best procedures in sustaining the audit opinion. At the same time, the auditor must maintain his independence, objectivity and professionalism (marked by competence) unaffected throughout his entire mission and not be an accomplice to committing criminal economic deeds.
Research Methodology
This study aims to analyze the connection between the affiliation of the NYSE quoted companies to one of the four audit companies of Big 4 and the occurrence or the lack of financial frauds within audited companies. The methodological approach is a positivist one and is focused on the formulation and testing of some work hypotheses (Smith, 2003). By virtue of a deductive-inductive reasoning, in this study shall be substantiated a series of work hypotheses starting from the current knowledge level presented in the literature. These hypotheses will be validated by means of the obtained empirical results and which will lead to reaching the research objectives.
Formulation of Work Hypotheses
In his study, McFadden (2003) considers that the big financial scandals had a significant and negative impact on the auditors’ image, being thus necessary to take some measures which lead to minimizing the not-detection risk associated to the auditor in terms of professional competence. Fukukava et al. (2011) note that, in order to maintain a high competence level of the auditors, the planning and the use of sufficient resources (qualified human, financial, time resources), which will contribute to diminishing the audit risk, are necessary. Hayes et al. (2005) thought that for the success of the financial audit mission, the mission responsibles must ensure a sufficient level of theoretical and technical training of the auditing team, the participation in all mission levels of the experienced members, the compliance with the legal and contractual terms, and the responsible application of the professional reasoning. Last but not least, the mission responsibles must also take into account the customer’s main activity when they perform tests for checking the financial standings accuracy (Hayes et al., 2005).
As far as the auditors’ role in preventing and detecting financial frauds is concerned, Bernardi (2009) provides a basis for evaluating the occurrence frequencies of the auditors’ observations regarding the clients’ integrity, and Bierstaker (2009) believes that the occurrence of fraud is mainly influenced by certain cultural factors. Jayalasksmy et al. (2005) asserts that the auditors have a great role in changing the ways of fighting financial fraud, and in this respect Bierstaker et al. (2006) tests the accountants’ perception (to a broad extent) of the fraud prevention and detection methods. Lennox and Pittman (2010) consider that a significant role is played in the big financial frauds by the audit company members of Big4 through their complicity. Hence, Pflugrath et al. (2007) maintains that imposing the professional ethical codes for auditors leads to the decrease of incompatibility, but also the support of the professional reasoning. Last but not least, Rezeaee (2004) asserts in his study that the trust recovery and the auditors’ image rehabilitation in front of public opinion must begin from within the accounting profession through the development of complex training programs against fraud.
Starting from the studies listed above regarding the auditor’s role and influence on the prevention and detection of financial frauds, the researchers consider as useful the testing of the following work hypotheses which will significantly contribute to the consolidation of the stakeholders’ trust in the big audit company members of Big 4.
Therefore, the researchers intend to test and validate the following expressed work hypotheses:
H1: A profile of the audited companies can be identified according to the incidence of financial frauds, in terms of the activity field and their affiliation to one of the audit companies of Big 4. The researchers thus intend to identify this profile.
H2: The affiliation of the audited companies to a certain audit company member of Big 4 in terms of the activity fields has a significant influence on the frauds incidence.
Methods of Data Analysis
In order to validate the work hypotheses and obtain the research results, the researchers suggest the use of multiple correspondences factorial analysis – MCFA and logistic regression analysis – LRA.
MCFA is a method of data analysis which permits the obtaining of profiles based on associations among three or several categorical variables. Initially suggested by Benzécri in 1969, MCFA is a method of multivariate analysis, being a general variant of the correspondences factorial analysis (Lebart at al., 2006). Applied in this case, the method implies for a sample of n companies audited by Big 4 values registered for m associated variables (e.g. status, auditor type, activity field), based on which the profile of a customer company from a certain group can be obtained, as a result of the study of the associations between the analyzed variables. This method synthesizes the initial information through the study of associations between variables. The associations are highlighted by a dispersion diagram on a system of factor axes ranked in descending order, according to their importance when the total variance of the cloud of points is explained (Jaba and Robu, 2009). The method permits the obtaining of factorial axes which characterizes the profile sizes. The two dimensions represented in the study are a linear combination of the analyzed category variables, according to the occurrence frequencies of the characteristics of each considered variable.
In order to establish the probability of fraud occurrence, according to a series of determining factors, the use of LRA is suggested. This method is based on the regression models with dependent alternative variables, such as: Y = β0 + β1X1 + β2X2 + ε, where Y = 0 if the company is not defrauded and Y = 1 if the company is frauded. In this respect, the values of Y characterize the status of the audited company, βi represents the coefficients of the logistic regression model (i = 1…2) and ε is the error component. Since Y is a Bernoulli-type variable (Gujarati, 2004), the values zero and one are associated to the occurrence probability: p for Y = 1 and q for Y = 0. At LRA the conditioned average (M(Yi/Ci) = pi) is based on a logistical repartition: M(Yi/Xi) = pfrauded = 1/[1+e^-(β0+βiXi)] = 1/(1+e^-zi). By applying the reversed function, zi = ln[pi/(1-pi)] will result, and the logistical model will be defined by the relation Li = ln[pfrauded/(1-pfrauded)] = β0+β1X1+ β2X2 + εi (Gujarati, 2004).
Variables Analyzed in the Study
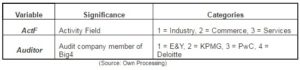
Based on the suggested work hypotheses, a series of independent variables (factors) have been analyzed in this study, synthesized in Table no. 1, with an influence on the status of the audited company (defrauded/not defrauded).
Table no. 1. Categorical Independent Variables Used in the Study
Target-population and Sample
The population that need to be learned about (target population) is represented by the totality of the NYSE quoted companies. From this population, a random sample of 200 companies was extracted and divided in two equal subsamples (100 frauded companies and 100 non frauded companies).
The subsample made of the defrauded companies presents 100 internationally famous cases during 2000-2002. The survey basis of this subsample is a list of 919 defrauded companies considered by Ketz (2003) in his work. Out of the 919 cases, we picked the ones that took place between 2000 and 2002 (201 defrauded companies in 2000, 225 companies in 2001 and 125 companies in 2002) and proportionally extracted 35 companies for 2000, 41 for 2001 and 24 for 2002, summing up 100 defrauded companies.
The subsample made of the 100 not defrauded companies has as survey basis the list of the companies of Top 500 Fortune for 2011. The first 100 companies were chosen from the 500 listed companies, except for the ones in the domain of investment funds and insurances.
It must be mentioned that in the case of defrauded companies, it was considered the auditor with whom the company had a signed contract in the year when the fraud was committed, and in the case of not defrauded companies the auditor with whom the company had signed the contract in 2011, the audit companies being members of Big 4 in both cases.
The structuring of the analyzed sample according to the activity field of the companies, the presence or absence of fraud, is highlighted in Picture 1.
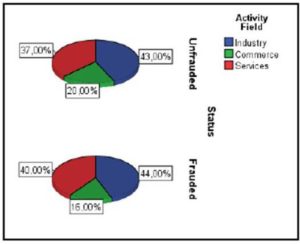
Figure no. 1: The Structure of the Two Subsamples Analyzed According to the Activity Field
(Source: Own Processing)
On the level of the entire sample were registered 43.50% companies in the industry field, 18.00% companies in the commerce field and 38.50% companies in the services field.
Data Collecting
The data regarding the analyzed companies were extracted from the financial standings of each company. EDGAR (Electronic Data Gathering Analysis and Retrieval), the online database of SEC (U.S. Securities and Exchange Commission), was used to identify the activity field and the auditor during the period considered in the study. Data processing has been carried out by means of the statistical software SPSS 19.0.
Research Results and Discussions
As a result of MCFA application on the data in the analyzed sample, a profile of the NYSE quoted companies will be obtained, according to the incidence of financial fraud on them, the affiliation to a certain auditor and the activity field of the companies. Although the maximum number of dimensions on which this profile can be characterized equals the number of observations minus one, the researchers will deal with the first two dimensions for an easy interpretation. They significantly explain the homogeneity/inertia of the cloud of points (the individuals graphically represented in the axes system associated to the two dimensions).
Table no. 2 Descriptive Statistics and Components Matrix
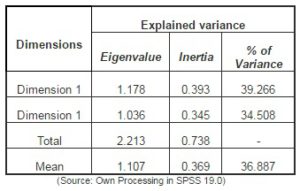
According to the data in table 2, the two dimensions explain 73.8% of the inertia of the points cloud characterized by the graphical representation of the statistical observations (taking into account the status type, the affiliation to a Big 4 auditor and the affiliation to an activity field). Moreover, dimension 1 explains 39.266% of the total variance at sample level (with an associated eigenvalue of 1.178), and the dimension 2 explains 34.50% of the total variance of the sample (with an eigenvalue of 1.036).
In the coordinates system Dimension 1 and Dimension 2, in Picture no. 2 the profile of a NYSE quoted company is obtained according to the status (defrauded/not defrauded), the affiliation to a certain Big 4 auditor and the activity field. Moreover, the closeness of the characteristics (the values of the categorical variables) to the axes origin means that most of the companies have those characteristics.
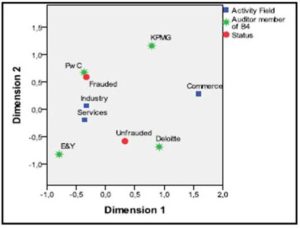
Figure no. 2 The Graphical Representation of the Defrauded/Not Defrauded Companies Profile
(Source: Own Processing in SPSS 19.0)
Based on the information obtained in the above diagram, it can be concluded that most of the companies both defrauded and not defrauded are from the industry and services field. In contrast to these, the companies in the commerce field had the least reported fraud cases. In order to outline the profile of a defrauded company, it is observed that they mostly belong to the industry and services field and (mostly) audited by PwC and less by E&Y, KPMG and Deloitte. The not defrauded companies belong to the commerce field and were audited by E&Y and Deloitte.
Table no. 3 The Influence of Variables on Discrimination
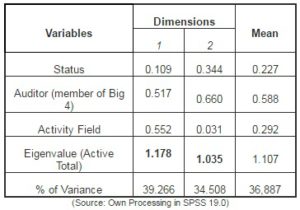
The influence of each variable on the two dimensions and thus the discrimination between the considered categories can be assessed based on the data in table 3. The status variable influences 10.9% of the variance explained by Dimension 1 and 34.4% of the variance explained by Dimension 2. One can therefore notice that there are significant differences between the defrauded and not defrauded companies. The affiliation of the companies to a certain auditor member of Big4 determines to 51.7% of the variance explained by the first dimension and 66% of the variance explained by the second dimension. At activity field level, one can notice that there are significant differences among the studied companies, the variance explained by Dimension 1 being influenced 55.2% by the activity field, and in the case of Dimension 2 the influence is only 3.1%. The summing up of these influences, for each dimension, determines the eigenvalue, associated to each dimension: 1.178 = 0.109 + 0.517 + 0.552 and 1.035 = 0.344 + 0.660 + 0.031.
The graphical representation of the variables influences the two dimensions and discrimination at the level of companies in the analyzed sample can be observed by means of the diagram in picture no. 3. Based on the graphical representations, one can observe that the greatest influence on discrimination has the affiliation of companies to a certain auditor member of Big4. In this respect, one can conclude that the fraud incidence is justified not by the activity level of the defrauded companies, but by the affiliation to the Big 4 auditors. Therefore, at the level of the analyzed sample, the origin of the fraud risk can be associated with the auditor’s complicity or his incapacity to detect certain irregularities, and not necessarily with the inherent risk coming from the affiliation of the company to one of the considered activity fields.
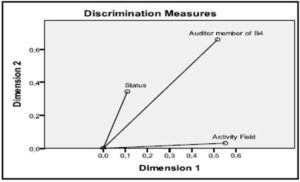
Figure no. 3 The Graphical Representation of the Influences of Variables on Dimensions
(Source: Own Processing in SPSS 19.0)
Knowing the influence of the affiliation of the customer companies on one of the audit companies can be highlighted by the synthesized data in table 4.
Table no. 4 The Influence of the Affiliation to a Certain Auditor on Fraud Occurrence
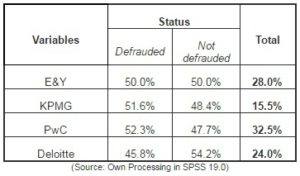
Based on the data in the above table, it can be noticed that most of the companies in the analyzed sample were audited by PwC (32.5%) and the least by KPMG (15.5%). In the sample PwC has the biggest number of defrauded companies (52.3%), and the lowest number of defrauded companies is registered by Deloitte (45.8%). One can notice the interesting situation of the companies audited by E&Y, where the number of the defrauded companies equals that of the not defrauded ones. One can thus conclude that most cases belong to the companied audited by PwC, as a result of the reported frauds. This fact questions the auditor’s independence and competence when prevention and detection of financial frauds are involved, and can signal his complicity to their committment or concealment.
In order to determine and quantify the influence of the affiliation of the audited company on one of the 4 audit companies considered in the study, the logistic regression analysis with dichotomic variables will be used. In this respect, the Auditor variable (member of Big 4) will be transformed into 3 new, alternative, dummy-type variables: D_E&Y, D_KPMG, D_PwC. According to Gujarati (2004), the number of the dummy variables obtained from a categorical variable equals the categories number of that variable minus 1, the last variant (Deloitte) will be chosen as reference. In this case: 4 categories -1 = 3 new variables.
The influence of the affiliation of the audit company on one of the 4 considered audit companies on the financial fraud occurrence can be synthesized in table 5.
Table no. 5 The Auditor’s Influence on the Occurrence of the Financial Fraud
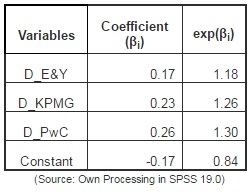
In the above table the coefficients of the regression model are estimated, as well as the influence of the affiliation to a certain audit on the occurrence of financial fraud. In the logistic model the sign of the coefficient value (βi) indicates the positive or negative influence on fraud committing according to the company member of Big4, which performs the financial audit, and the quantification is determined based on the exponential of the (exp(βi)) coefficient. Therefore, the logistic regression model will look as follows:
ln[pfrauded/(1-pfrauded)] = -0.17 + 0.17D_E&Y + 0.23D_KPMG + 0.26D_PwC + εi. (1)
The obtained results indicate the fact that signing an audit commitment with Deloitte results in the decrease of chances that the audited company is defrauded (due to the auditor’s incapacity to detect fraud or his complicity; the constant value of -0.17 is the value associated to the reference category, Deloitte). The companies audited by PwC, followed by the ones audited by KPMG and E&Y have the highest chances of being defrauded. Furthermore, a company audited by Deloitte has 16% (0.84 – 1) chances to be defrauded, while the companies audited by PwC have up to 30% (1.30 – 1) additional chances to be defrauded (total 46% = 16% + 30%). At the same time, the companies audited by KPMG have 42% chances to be defrauded (16% + 26%), and the companies audited by E&Y, 34% (16% + 18%). From these results, one can conclude that the audit company Deloitte has the highest trust degree as far as the lack of complicity at committing or concealing the frauds is concerned.
Based on the same approach, the researchers will also introduce the Activity Field variable into the analysis, turned into two new, dummy-type variables (D_Industry și D_Commerce), whereby the Services variant is considered a reference. As a result of the SPSS processing, the obtained results are synthesized in table 6.
Table no. 6 The Influence of the Auditor and the Activity Field on the Occurrence of Financial Fraud
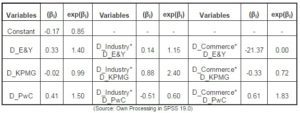
According to the same reasoning as for the data synthesized in table 5, the new regression model will be as follows:
ln[pfrauded/(1-pfrauded)] = -0.17 + 0.33D_E&Y -0.02D_KPMG + 0.41D_PwC + 0.14D_Industry* D_E&Y + 0.88D_Industry*D_KPMG -0.51D_Industry*D_PwC –21.37D_Commerce D_E&Y -0.33D_Commerce*D_KPMG + 0.61D_Commerce*D_PwC + εi. (2)
The above model synthesizes the concomitant influence of the affiliation on a certain auditor and the activity development in a certain activity field. In the above model, obtained by means of dummy-type alternative variables, the yellow marked part represents the model for the companies in the services field (reference field) which are audited by the Big 4 companies, the red marked part represents the model for the companies in the industry field, and the blue marked part represents the model for the companies in the commerce field. The coefficients of the model are synthesized in table 5 and based on which one can appreciate the influence of the considered variables on the chances of fraud occurrence at audited companies level. The sign of the coefficients attached to the variables considered in the model indicate the sense and the intensity of the influence on the chances increase or decrease to be defrauded or not. In this respect, the companies in the commerce field and audited by E&Y have the lowest chance to be defrauded (-21.37), while the affiliation of the commerce companies to PwC (0.61) or the industry ones to KPMG significantly contributes to the increase of the chances to be defrauded. Frauds may occur either due to the auditor’s complicity or his incapacity to evaluate the control system which contributes to the detection and prevention of frauds.
Moreover, in order to determine the chances of a company from a certain activity field and audited by one of the companies members of Big4 to be frauded the variables in the model shall be replaced with specified values. Therefore, in the case of the company in the services field, audited by Deloitte, we will have: D_Industry = 0, D_Commerce = 0, D_E&Y = 0, D_KPMG = 0, D_PwC = 0, and the model will be as follows: ln[pfrauded/(1-pfrauded)] = -0,17 => pfrauded/(1-pfrauded) = exp(-0,17) => pfrauded/(1-pfrauded) = 0.85 => pfrauded = 0.45, so the chance of a company featuring these characteristics to be defrauded is 45.9%.
In the case of the company in the commerce field audited by E&Y, we will have: D_Industry = 0, D_Commerce = 1, D_E&Y = 1, D_KPMG = 0, D_PwC = 0, and the model will be as follows: ln[pfrauded/(1-pfrauded)] = -0.17 + 0.33 -21.37=> pfrauded/(1-pfrauded) = exp(-0.17 + 0.33 -21.37) => pfrauded/(1-pfrauded) = exp(-21.22) = 0.00 => pfrauded = 0.00, so the chance of a company featuring these characteristics to be defrauded is 0%.
Last but not least, as in the case of model (1), the exponential value of the coefficients determines the influence of the considered dummy variables (in this case the affiliation to a certain auditor and the activity field) on the chances to be defrauded or not.
As a conclusion, it can be estimated that based on the obtained models (1 and 2), the chances of a defrauding or not a company can be established, according to the considered factors, the information being useful to the stakeholders in choosing the auditors, and appreciating the independence, objectivity and professional competence degree of the audit company, which issues the audit opinion in the final report.
Based on the presented results, the identification of the profile and the estimation of the factor influence of the financial fraud incidence on the NYSE quoted companies, audited by the Big4 audit companies, the two work hypotheses are proved to be true, meaning that there is a significant connection between the chance of a company in a certain activity field to be defrauded and the affiliation to a certain Big4 auditor.
Conclusions
In the context of the big financial scandals, the auditor’s role is that of a guarantor of the financial standings accuracy, and is also a main actor in preventing and detecting them. The famous cases of financial fraud (mostly during Enron-Arthur Andersen time) proved that the auditor’s responsibility regarding the prevention and detection of frauds was often obstructed by the incapacity to detect them, or, even worse, by his complicity.
The empirical results have validated the two proposed work hypotheses: the identification of a NYSE quoted company profile (defrauded and not defrauded), but also the estimation of the factors influence on the financial fraud occurrence.
It can be concluded from the obtained results that there is a significant connection between the occurrence of financial frauds and the affiliation to a certain auditor (member of Big4). Therefore, the companies audited by PwC featured a high incidence of financial frauds, while the companies audited by E&Y featured less cases of financial fraud. The question now, being a subject of further researches in the field, refers to what caused the occurrence of financial fraud among the customers audited by the companies members of Big 4. In this case, two new hypotheses can be considered: either the auditor’s complicity or his incapacity to detect significant deviations.
Last but not least, the critical activity fields haven been identified, which favor the occurrence of the frauds correlated to the affiliation to a certain auditor. Fields such as services, whose benefits are difficult to quantify (including evaluating and inventory), and industry (where the lack of advanced protection control and protection policies results in assets evasion) are propitious to financial fraud. Opposite to these, according to the analyzed sample, the commerce field features the lowest fraud incidence (both assets evasion and in the fraudulent financial reporting).
Moreover, based on the proposed logistic regression models, it can be observed that, although in some cases the activity field of the audited company is an essential component of the fraud risk, the affiliation to a certain auditor can increase or diminish this risk. In this respect, the auditor’s competence to detect frauds is involved (the specialization in an activity field, or the acquaintance with and the recognition of financial fraud schemes). Another factor which can increase the manifestation of financial fraud according to the affiliation to a certain auditor is also the auditor’s complicity to the concealment or producing of the financial fraud. The independence and objectivity criteria are in this case obviously infringed.
The future directions of the study try to identify the main causes for each auditor (member of Big 4), which resulted in the occurrence of financial fraud. Moreover, models can be obtained, that can indicate the connection between the type of fraud (assets evasion or fraudulent reporting) and a series of factors (activity field, the auditor’s competence or complicity, the efficiency of the internal control system).
The limits of the study are marked by the attempt to establish just the existence of a connection between the presence or absence of fraud and the affiliation to the audit companies of Big4. This indicates that in some causes also the auditors are responsible for the manifestation of criminal economic and financial deeds. However, the objectives of the research are not aimed to identify the causes behind the auditor’s involvement. Overall, the researchers consider that the subject as well as the obtained results can be of great help to all stakeholders in making an opinion of the service quality offered by the Big 4 companies, and evaluating the extent to which the users of the financial accounting information can rely on the opinion formulated by auditors.
Last but not least, the use of statistical methods within the financial audit mission, as well as the interconnection between the results and the financial analysis and accounting may open a new research direction. This new field, aiming to analyze the economic and financial phenomena within the financial audit, based on some indicators of financial analysis by means of advanced statistical and econometrical methods, is hypothetically called auditometrics.
Acknowledgements
This work was supported by the European Social Fund in Romania, under the responsibility of the Managing Authority for the Sectoral Operational Programme for Human Resources Development 2007-2013 [grant POSDRU/CPP 107/DMI 1.5/S/78342].
(adsbygoogle = window.adsbygoogle || []).push({});
References
Ball, R. (2009). “Market and Political/ Regulatory Perspectives on the Recent Accounting Scandals,” Journal of Accounting Research, 47 (2), pp. 277- 323.
Publisher – Google Scholar
Bernardi, R. A. (2009). “Establishing A Baseline for Assessing the Frequency of Auditor’s Comments Concerning Perceived Client Integrity,” Managerial Auditing Journal, 24 (1), pp. 4-21.
Publisher – Google Scholar
Bierstaker, J. L., Brody, R. G. & Pacini, C. (2006). “Accountants’ Perceptions Regarding Fraud Detection and Prevention Methods,” Managerial Auditing Journal, 21 (5), pp.520-535.
Publisher – Google Scholar – British Library Direct
Bragg, S. M. (2010). Practitioner’s Guide to GAAS 2010: Covering all SASs, SSAEs, SSARSs, and Interpretations, John Wiley & Sons, New Jersey.
Publisher
Carpenter, T. D. (2007). “Audit Team Brainstorming, Fraud Risk Identification, and Fraud Risk Assessment: Implications of SAS No. 99,” The Accounting Review, 82 (5), pp. 1119-1140.
Publisher – Google Scholar – British Library Direct
Cheng, X., Crabtree, A. D. & Smith, D. B. (2009). “Disclosure of Allegedly Illegal Corporate Activities and Information Risk,” Advances in Accounting, incorporating Advances in International Accounting, 29, 136-146.
Publisher – Google Scholar
Cressey, D. R. (1953). “Other People’s Money: A Study in the Social Psychology of Embezzlement,” Glencoe, 1II: Free Press Press.
Publisher – Google Scholar
Dowler, F. & Harris, E. M. (1912). ‘Auditing, Accounting and Banking: A Manual for Accountants, Advanced Book-keeping Students, and Business Men,’ Sir Isaac Pitman & Sons, London.
Google Scholar
Fukukawa, H., Mock, T. J. & Wright, A. (2011). “Client Risk Factors and Audit Resource Allocation Decisions,” 47 (1), pp. 85- 108.
Publisher – Google Scholar
Gallet, O. (2010). ‘Halte Aux Fraudes. Guide pour auditeurs et dirigeants,’ 2e édition, Dunod, Paris.
Google Scholar
Gujarati, D. (2004). ‘Basic Econometrics,’ the McGraw-Hill Companies, New York.
Hayes, R., Dassen, R., Schilder, A. & Wallage, P. (2005). Principles of Auditing. An Introduction to International Standards of Auditing, 2nd edition, Ed. Pearson Education.
Publisher
Huang, H.- W. (2009).”Sarbanes-Oxley Section 404 Compliance. Recent Changes in US-Traded Foreign Firms’ internal control reporting,” Managerial Auditing Journal, 24 (6), pp. 584-598.
Publisher – Google Scholar
International Federation of Accountants (IFAC) (2009). ‘International Standards on Auditing,’.
Jaba, E. & Robu, I.- B. (2009).”Utilizarea Analizei Discriminant Pentru Obtinerea Probelor de Audit (I),” Audit Financiar, 7 (11), pp. 20-24.
Publisher – Google Scholar
Jayalasksmy, R., Seetharaman, A. & Khong, T. W. (2005). “The Changing Role of the Auditors,” Managerial Auditing Journal, 20 (3), pp. 249-271.
Publisher – Google Scholar
Ketz, J. E. (2003). ‘Hidden Financial Risk: Understanding Off-Balance Sheet Accounting,’ John Wiley & Sons, New Jersey.
Google Scholar
Krambia-Kapardis, M. (2002). “A Fraud Detection Model: A Must for Auditors,” Journal of Financial Regulation and Compliance, 10 (3), pp. 266-278.
Publisher – Google Scholar – British Library Direct
Lebart, L., Piron, M. & Morineau, A. (2006). ‘Statistique Exploratoire Multidimensionnelle. Visualisation et inférences en fouille de données,’ 4e édition, Dunod, Paris.
Google Scholar
Lenard, M. J. & Alam, P. (2009). “An Historical Perspective on Fraud Detection: From Bankruptcy Models to Most Effective Indicators of Fraud in Recent Incidents,’”Journal of Forensing & Investigative Accounting, 1 (1), pp. 1-27.
Publisher – Google Scholar
Lennox, C. & Pittman, J. A. (2010). “Big Five Audits and Accounting Fraud,” Contemporary Accounting Research, 27, pp. 209-247.
Publisher – Google Scholar
Limperg institute (1985). The Social Responsibility of the Auditor, Amsterdam.
Publisher – Google Scholar
McFadden, J. E. (2003). ‘Client and Engagement Acceptance: Only A Public Company Audit Service Concern?,’ The Practicing CPA, 27(6), pp. rmr3-rmr4.
Pflugrath, G., Martinov-Bennie, N. & Chen, L. (2007). “The Impact of Codes of Ethics and Experience on Auditor Judgments,” Managerial Auditing Journal, 22 (6), pp. 566-589.
Publisher – Google Scholar – British Library Direct
Pickett, S. (2006). Audit Planning: a Risk-Based Approach, John Wiley & Sons Inc, New Jersey.
Publisher – Google Scholar
Rezaee, Z. (2004). “Restoring Public Trust in the Accounting Profession by Developing Anti-Fraud Education, Programs, and Auditing,” Managerial Auditing Journal, 19 (1), pp. 134-148.
Publisher – Google Scholar – British Library Direct
Rezaee, Z. & Riley, R. (2009). Financial Statement Fraud: Prevention and Detection, 2nd edition, John Wiley & Sons, New Jersey.
Publisher
Russell, G. (2009). ‘Corporate Governance and Its Relevance to Audit Quality’ published: Institute of Directors (2009),’ The Handbook of International Corporate Governance. A Definitive Guide, 2nd edition, Kogan Page, London and Philadelphia.
Seow, J.- L. (2009). “Cue Usage in Financial Statement Fraud Risk Assessments: Affects of Technical Knowledge an Decision Aid Use,” Accounting and Finance, 49, pp. 183-205.
Publisher – Google Scholar
Silverstone, H. (2005). Fraud 101: Techniques and Strategies for Detection, 2nd edition, John Wiley & Sons, New Jersey.
Publisher – Google Scholar
Singleton, T. W. & Singleton, A. J. (2010). Fraud Auditing and Forensic Accounting, 4th edition, John Wiley & Sons, New Jersey.
Publisher – Google Scholar
Smith, M. (2003). Research Methods in Accounting, SAGE Publication, London.
Publisher
Soltani, B. (2003). ‘Auditing: An International Approach,’ Prentice Hall, Pearson Education, Essex.
Walton, S. & Kimball, D. S. (1916). ‘Auditing and Cost Finding,’ Alexander Hamilton Institute, New York.
Google Scholar
Watts, R. L. & Zimmerman, J. L. (1979). “The Demand for and Supply of Accounting Theories: The Market for Excuses,” The Accounting Review, (April), pp. 273-305.
Publisher – Google Scholar











